Cyber Security is a concern for many organizations for a variety of reasons. Typically, these concerns include – how do we detect and stop attacks, strengthen security across our key systems, and keep data secure. Often an attempt to address these concerns, leads with “where do we start?”.
To address these concerns, Calance launched a Cyber Security Assessment Services to assess an organization’s information security posture and find best value for your company's time, money and efforts. The assessment methodology is aligned to ISO 270001 or NIST framework and can cover all or selected domains. The model utilizes Capability Maturity Model (CMM) used to assess people, processes and technology.
The assessment is divided in 3 steps:
Step 1: Current State Analysis
- An assessment of Information Security Controls across People, Process and Tools aspects of an organization. The scope of assessment can be customized to only include certain subject areas.
- The assessment methodology is based on industry standards that are customized to match your industry, challenges and scope.
Step 2: Target State Definition
- Recommendations to improve information security in the identified areas.
- Allows you to only select recommendations that suit your information security maturity aspirations.
- Recommendations based on best practices from well-established information security standards.
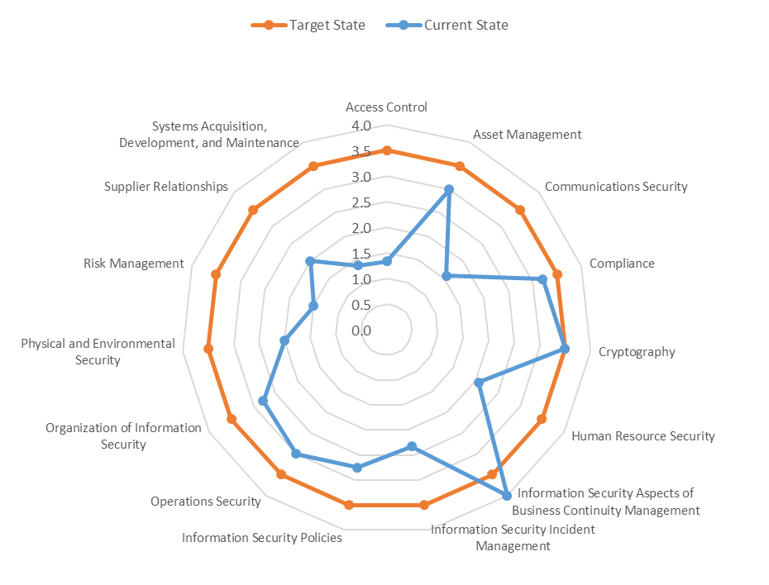
(Diagram Presented as a Sample)
- Assessment scope can be customized to include all domains or specific areas
- Target state identified based on client discussions represented on spider diagram
- Model support both self-assessment and in-person interviews
- Recommendations aligned to assessed scope and information security maturity aspirations
Step 3: Roadmap
- An approach to prioritize investments in the identified improvement areas based on your organization's business, IT and information security objectives.
- Proposed across short, medium and long term.
Outcome:
The outcome of this process is knowing the state of your current security landscape through:
- Visibility into your IT security
- Control over your IT Security budget; and
- More resilience in facing cyber security challenges, both inside and outside the organization
Learn more about our affordable Cyber Security Assessment.

